Some of the Ransomware attacks in 2022
Cisco
Networking giant Cisco, which specializes in cybersecurity and incident response services with Cisco Talos, confirmed it was attacked by the Yanluowang ransomware gang on May 24 after threat actors gained access to an employee’s credentials through a compromised personal Google account. Nick Biasini, global lead of outreach at Cisco Talos, detailed the attack that revealed a successful voice phishing campaign letting attackers bypass the multifactor authentication settings. However, Cisco apparently detected the intrusion before threat actors could deploy the ransomware. In a September update, Cisco confirmed stolen data posted to Yanluowang’s public data leak site matched what Cisco had “already identified and disclosed.”
San Francisco 49ers
Two days after being listed on BlackByte’s public leak site, the San Francisco 49ers confirmed it suffered a ransomware attack in a statement to The Record on Feb. 13 — Super Bowl Sunday. Law enforcement was contacted immediately, and the NFL team said it believed the attack was limited to its corporate network. Following an investigation with law enforcement that concluded on Aug. 9, the popular NFL franchise started sending out data breach notifications to affected customers. The attack was just one of several in February against major enterprises.
Glenn County Office of Education
The Glenn County Office of Education (GCOE) in California was one of many ransomware victims in the education sector last year. GCOE was struck by an attack on May 10 that limited network access. According to a DataBreaches.net report, GCOE paid a $400,000 ransom to the Quantum ransomware gang. In October, the office that serves eight school districts began sending out data breach notifications to current and former students as well as teachers whose data may have been stolen. Information included names and Social Security numbers.
Opus Interactive, Inc.
Hosting service provider Opus Interactive, Inc., also suffered a ransomware attack in May. On its interactive status page under May, the Oregon-based vendor said there was an “incident affecting its infrastructure” but that all its customer’s workloads were restored successfully.
On May 13, Oregon Live reported that the Oregon Secretary of State’s office was one of Opus’s customers. Campaign finance records stored on Opus systems were subsequently moved ahead of Oregon’s primary election. On May 25, Opus updated the incident status page to “resolved.”
Entrust Corporation
In early June, certificate authority giant Entrust Corporation, which provides authentication and identity management technology, was hit by LockBit ransomware. While no official statement was released, the attack was confirmed by BleepingComputer and security researcher Dominic Alvieri, who shared a letter Entrust president Todd Wilkinson sent to employees.
Wilkinson did not specify ransomware was involved but did confirm data was exfiltrated. In August, Entrust appeared on LockBit’s public data leak site used to pressure victims into paying. Entrust customers include “some of the biggest companies in the world,” according to its website, including Microsoft, VISA and VMware.
Macmillan Publishers
Later in June, a ransomware attack temporarily disabled Macmillan Publishers’ ability to accept, process or ship orders. Publishers Weekly was the first to report the incident on June 28 after obtaining emails from Macmillan that a “security incident, which involves the encryption of certain files on our network” caused operations to remain closed. A separate report by BleepingComputer confirmed employees were unable to access their emails. Based in New York, Macmillan operates in over 70 countries with eight divisions in the U.S.
Models and Policies to take into account
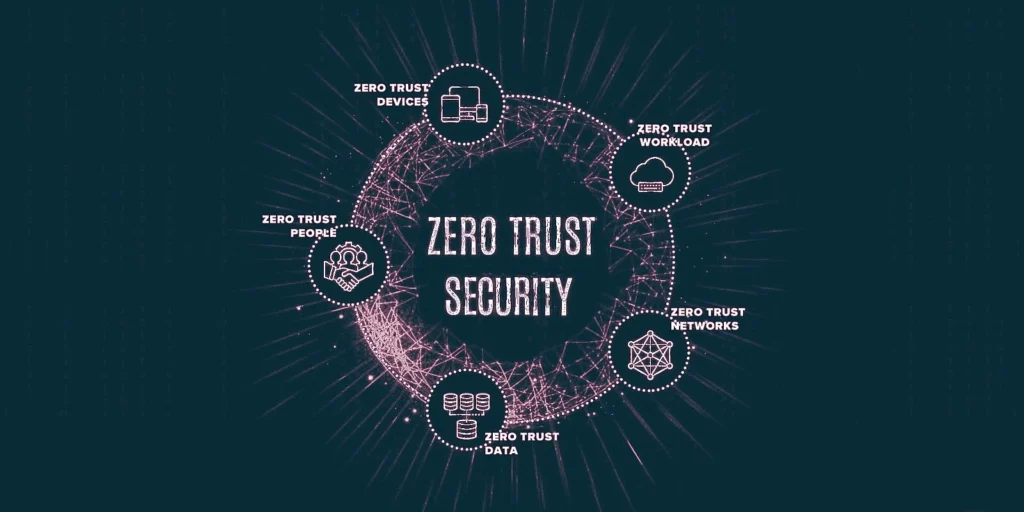
As the threat of ransomware continues to grow and evolve, it is more important than ever that we adopt a Zero Trust model and policies for best practices to combat this threat.
The Zero Trust model is based on the principle that we should not automatically trust any device, user, or network, even if they are within our own network perimeter. Instead, we should always verify the identity and intent of every request for access, and only grant access if it is determined to be safe and legitimate.
One of the key components of a Zero Trust model is the implementation of multi-factor authentication, which ensures that only authorized individuals are able to access sensitive information. This can be done through the use of a password, a fingerprint, or even a facial recognition scan.
Another important component of a Zero Trust model is the implementation of segmentation, which divides our network into smaller, isolated segments. This makes it more difficult for ransomware to spread, as it is unable to move laterally between segments.
Additionally, it is important to have an incident response plan in place, so that if a ransomware attack does occur, we are able to quickly and effectively respond to contain and eliminate the threat.
To implement Zero Trust model it’s important to have regular security assessments and penetration testing to identify vulnerabilities in our network and devices, and then take steps to remediate them. It’s also important to ensure that all devices, software and operating systems are kept up-to-date with the latest security patches.
The Zero Trust model is a comprehensive approach to security that helps to protect our organization from the ever-evolving threat of ransomware. By implementing these best practices, we can ensure that our data and systems remain safe and secure.
“Adopting a Zero Trust model and implementing best practices is not only a proactive measure against the threat of ransomware, it is a vital step in ensuring the security and integrity of our organization.”
Julio Verissimo
President & CEO – Borderless Consulting
Contact us to know more