
In today’s rapidly evolving digital landscape, cybersecurity has become a paramount concern for individuals and businesses alike. The ever-growing reliance on technology and interconnected networks exposes us to various cyber threats, making it essential for us to adopt robust cybersecurity measures. This aims to shed light on the importance of cybersecurity and how Borderless Consulting can help fortify your digital defenses. (Some examples of sofisticated attacks pictures below first 2 pictures example of powerless backdoor attack, the after its how the attack can abtain all information to enter corporate network)
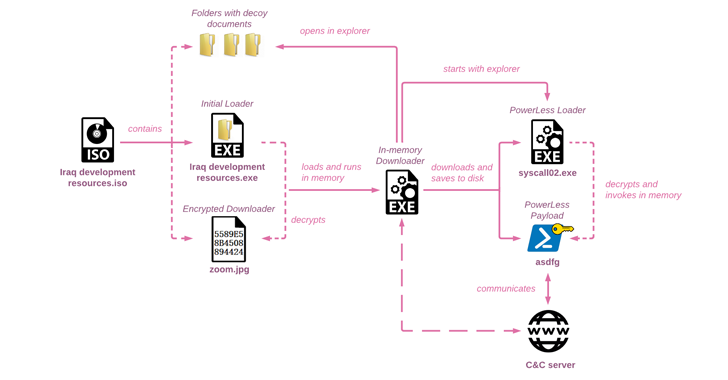
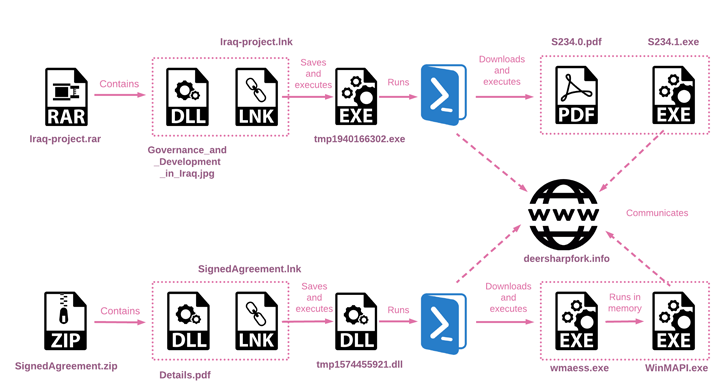
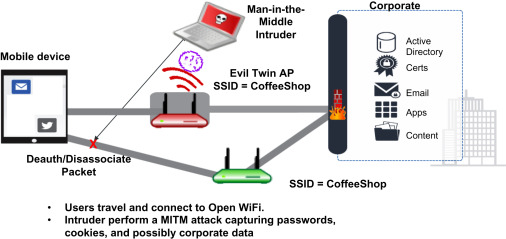
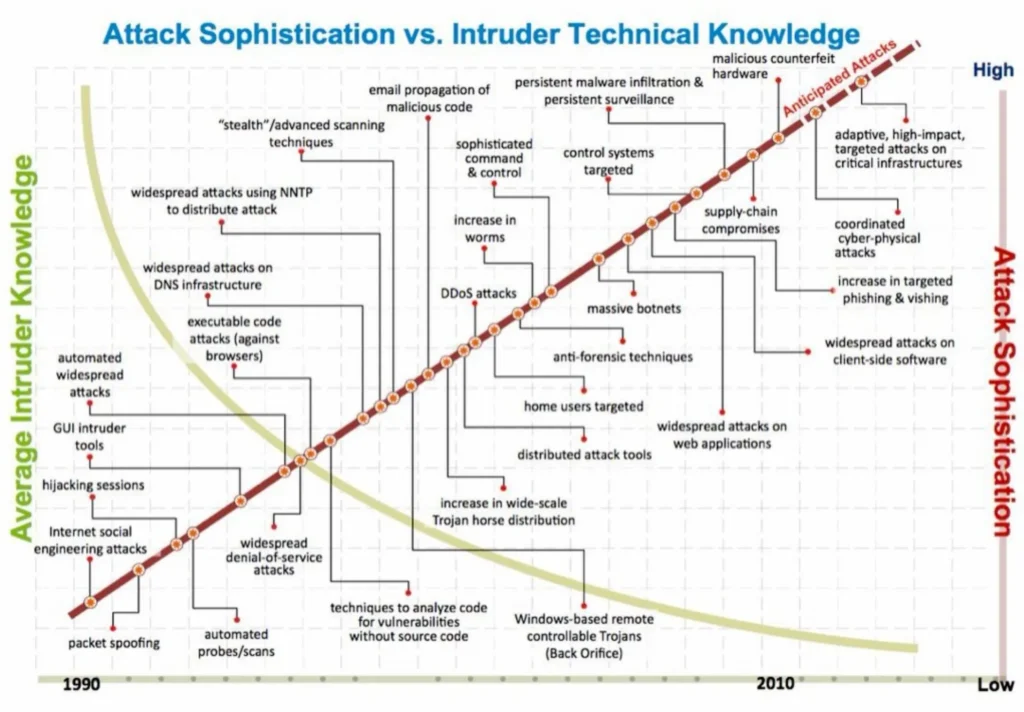
We dive into the ever-evolving cybersecurity landscape. The digital era has brought unprecedented convenience, but it has also exposed us to an array of cyber threats. The motives behind cyberattacks vary from financial gain to espionage, activism, or simply causing disruption. Cybercriminals target both individuals and organizations, seeking to compromise sensitive data, disrupt services, and tarnish reputations. Advanced hacking attacks have emerged as a grave concern, posing significant threats to individuals and organizations alike. These sophisticated cyber threats exploit vulnerabilities in our interconnected networks and systems, leading to severe consequences such as data breaches, financial losses, and reputational damage. As cybercriminals continuously evolve their tactics, it is crucial to adopt proactive measures to stay ahead and safeguard our digital assets effectively.
Borderless Consulting stands as a trusted partner in the battle against advanced hacking attacks. With their extensive expertise in cybersecurity and comprehensive understanding of the ever-changing threat landscape, we offer tailored solutions to address the unique challenges posed by these malicious activities.
One of Borderless Consulting’s core strengths lies in conducting in-depth vulnerability assessments and penetration testing. By identifying weaknesses in an organization’s systems and networks, they can proactively address potential entry points for cyber attackers. This proactive approach significantly reduces the risk of falling victim to advanced hacking attacks.
The multi-layered approach to network security and infrastructure protection provided by Borderless Consulting ensures that organizations have robust defenses in place. By deploying advanced firewalls, intrusion detection systems, and encrypted communication channels, they create formidable barriers against potential breaches, protecting sensitive data and ensuring smooth operations and recognizes the importance of the human element in cybersecurity. Through comprehensive employee training and awareness programs, they empower individuals to recognize and respond effectively to social engineering attempts and phishing attacks. Strengthening the human aspect of cybersecurity is instrumental in thwarting many entry points exploited by cybercriminals.
In the unfortunate event of a cyber incident, Borderless Consulting’s efficient incident response and disaster recovery plans come into play. By defining clear protocols and procedures, they ensure that any damage is contained and minimized, allowing for swift recovery and reduced downtime.
Moreover, compliance with industry-specific requirements and governmental regulations is paramount in protecting against advanced hacking attacks. Borderless Consulting’s dedication to staying up-to-date with evolving regulations helps organizations avoid legal repercussions and maintain their reputation. Borderless Consulting’s proactive approach to embracing emerging technologies strengthens defenses against the ever-evolving threat landscape. By integrating innovative solutions, such as AI-driven threat detection and blockchain-based authentication, they future-proof organizations’ cybersecurity strategies.
The threat of advanced hacking attacks demands a vigilant and proactive approach. Borderless Consulting’s tailored solutions, proactive assessments, employee training, advanced technologies, and comprehensive incident response plans all contribute to building a resilient cybersecurity strategy.
Understanding the Cybersecurity Landscape In this chapter, we explore the current state of cybersecurity, discussing the types of cyber threats, the motives behind cyberattacks, and their potential impact on individuals and organizations. It emphasizes the need for proactive measures to stay one step ahead of cybercriminals. Understanding the potential impact of cyber threats is crucial. A successful cyberattack can result in significant financial losses, damage to a company’s reputation, legal liabilities, and compromised customer trust. This chapter aims to underscore the urgency for proactive cybersecurity measures to prevent potential breaches and mitigate their consequences.
The Role of Borderless Consulting in Cybersecurity Here, we introduce Borderless Consulting, a leading international firm with cybersecurity division with a proven track record in providing comprehensive cybersecurity solutions. We delve into their mission, values, and expertise, establishing their credibility in the industry.
Borderless Consulting emerges as a reputable cybersecurity firm with a wealth of experience and expertise. Their mission is to safeguard organizations from cyber threats by delivering cutting-edge solutions and comprehensive protection. The company’s track record and testimonials from satisfied clients establish their credibility in the industry.
The success of Borderless Consulting lies in its highly skilled team of cybersecurity experts who stay updated with the latest threat vectors, security technologies, and best practices. By working with Borderless Consulting, organizations gain access to a wealth of knowledge and tailored solutions.
Tailored Cybersecurity Solutions Borderless Consulting understands that every organization’s cybersecurity needs are unique. We highlight the importance of personalized cybersecurity solutions and how Borderless Consulting excels in tailoring their services to meet individual requirements.
Cybersecurity is not a one-size-fits-all approach. Each organization has distinct assets, risk profiles, and compliance requirements. A cookie-cutter security solution is ineffective and leaves vulnerabilities unaddressed. This chapter highlights the importance of tailored cybersecurity solutions to match an organization’s specific needs.
Borderless Consulting excels in crafting customized security strategies, working closely with their clients to understand their unique challenges and objectives. By taking a personalized approach, they can identify potential weaknesses in an organization’s security posture and design effective countermeasures.
Vulnerability Assessments and Penetration Testing In this chapter, we discuss the significance of conducting vulnerability assessments and penetration testing to identify and address potential weaknesses in an organization’s network. We elaborate on how Borderless Consulting employs industry-leading techniques to uncover vulnerabilities and reinforce defenses.
To fortify an organization’s defenses, it is essential to identify vulnerabilities proactively. Vulnerability assessments and penetration testing play a pivotal role in this process. Vulnerability assessments help identify weaknesses in an organization’s systems and networks, while penetration testing simulates real-world attacks to gauge the effectiveness of existing security measures.
Borderless Consulting employs skilled ethical hackers to conduct thorough vulnerability assessments and penetration tests. By identifying and addressing vulnerabilities before malicious actors can exploit them, organizations can significantly reduce their risk exposure.
Network Security and Infrastructure Protection Protecting the network and infrastructure is vital to safeguarding sensitive data and ensuring smooth operations. This chapter explores the comprehensive network security solutions offered by Borderless Consulting, including firewalls, intrusion detection systems, and encrypted communication channels.
The network serves as the backbone of any digital operation, making it a prime target for cyberattacks. This chapter emphasizes the significance of robust network security measures and infrastructure protection to safeguard sensitive data and ensure uninterrupted operations.
Borderless Consulting provides an array of network security solutions, including advanced firewalls, intrusion detection systems, and encrypted communication channels. By deploying multi-layered defenses, they create a formidable barrier against cyber threats, enhancing an organization’s overall security posture.
Employee Training and Awareness Humans remain a significant factor in cybersecurity vulnerabilities. This chapter emphasizes the importance of educating employees about cybersecurity best practices and how Borderless Consulting conducts training sessions to raise awareness and foster a security-conscious culture within organizations.
Human error remains a significant factor in cybersecurity breaches. Employees can unintentionally become conduits for cyberattacks through social engineering or phishing attempts. Raising employee awareness about cybersecurity best practices is crucial to fostering a security-conscious culture.
Borderless Consulting conducts comprehensive training sessions to educate employees about common cyber threats and how to identify and respond to them. By empowering the workforce with knowledge, organizations can effectively reduce the risk of successful cyberattacks.
Incident Response and Disaster Recovery No matter how robust the defenses, cyber incidents can still occur. This chapter delves into the critical role of incident response and disaster recovery plans in mitigating the impact of cyberattacks. Borderless Consulting’s expertise in developing and implementing effective response strategies is showcased.
Despite robust preventive measures, cyber incidents can still occur. The key to minimizing their impact lies in an efficient incident response and disaster recovery plan. This chapter delves into the critical role of preparedness in mitigating the consequences of cyberattacks.
Borderless Consulting assists organizations in developing and implementing effective incident response and disaster recovery plans. By defining clear procedures and protocols, organizations can respond swiftly and effect
Compliance and Regulatory Support In today’s highly regulated environment, organizations must adhere to various cybersecurity standards and regulations. We explore how Borderless Consulting assists businesses in achieving compliance with industry-specific requirements and governmental regulations.
The modern business landscape is heavily regulated, with various cybersecurity standards and governmental regulations in place. Non-compliance can lead to severe penalties and reputational damage. This chapter emphasizes the importance of meeting industry-specific requirements and complying with relevant regulations.
Borderless Consulting provides comprehensive support to ensure organizations adhere to necessary compliance standards. By staying up-to-date with ever-changing regulations, they help clients navigate the complex landscape and avoid potential legal repercussions.
Securing the Future with Emerging Technologies The world of cybersecurity is continually evolving, and emerging technologies present both opportunities and challenges. This chapter discusses how Borderless Consulting stays ahead of the curve, embracing new technologies to bolster cybersecurity defenses.
As cyber threats continue to evolve, so must cybersecurity solutions. This chapter discusses the role of emerging technologies in bolstering cybersecurity defenses. From AI-driven threat detection to blockchain-based authentication, new technologies present both opportunities and challenges.
Borderless Consulting remains at the forefront of cybersecurity advancements, actively researching and adopting emerging technologies. By embracing innovative solutions, they enhance their ability to protect clients from evolving cyber threats.
The Road Ahead: Building a Resilient Cybersecurity Strategy In this final chapter, we recap the crucial elements of a robust cybersecurity strategy and how Borderless Consulting can partner with organizations to build a resilient cybersecurity framework for the future.
In this final chapter, we recap the essential elements of a resilient cybersecurity strategy. Combining tailored solutions, proactive vulnerability assessments, comprehensive employee training, and cutting-edge technologies, organizations can build a robust defense against cyber threats.
By partnering with Borderless Consulting, organizations gain a reliable ally dedicated to fortifying their digital defenses. As cyber threats continue to evolve, the collaboration with an experienced cybersecurity firm becomes increasingly critical to secure the future of the digital world. Together, we can navigate the ever-changing cybersecurity landscape and safeguard our digital assets from malicious actors.
Conclusion: Cybersecurity is a never-ending battle, and the stakes have never been higher. By working with Borderless Consulting, organizations can ensure they have a reliable ally in the fight against cyber threats. With their expertise, tailored solutions, and commitment to staying at the forefront of cybersecurity advancements, Borderless Consulting stands ready to secure the digital world and protect businesses from the ever-evolving threat landscape.
“In this digital age, the cybersecurity landscape is ever-evolving, and the need for comprehensive protection has never been more crucial. Borderless Consulting emerges as a formidable ally, providing tailored solutions to address the unique challenges each organization faces. By understanding the potential impact of cyber threats and implementing proactive measures, we fortify our defenses and minimize the risk of devastating breaches. Through thorough vulnerability assessments and advanced penetration testing, Borderless Consulting ensures that vulnerabilities are addressed before adversaries can exploit them. With a multi-layered approach to network security and robust infrastructure protection, sensitive data remains safe, and operations run smoothly. But it doesn’t stop there. By fostering a security-conscious culture through employee training, organizations fortify their first line of defense against social engineering and phishing attempts. And in the event of a cyber incident, Borderless Consulting’s efficient incident response and disaster recovery plans reduce downtime and data loss. Compliance with regulations is diligently maintained, safeguarding the organization from legal repercussions. Embracing emerging technologies, Borderless Consulting stays ahead of the curve, future-proofing our defenses against the ever-changing threat landscape. Together, we build a resilient cybersecurity strategy, securing the digital world for a safer future.”
Julio Verissimo – President & CEO
Borderless Consulting

